Side Channel
Side channel
Steal Secret through side channels
side channels: timing; power; em emissions; sound; heat; cache
Infer secrets via secret-dependent physical information #### Example
RSA Decryption Algorithm
1 | for bit in k: |
square | square | square & multiply |
square & multiply | ...
0 | 0 | 1 | 1 | ...
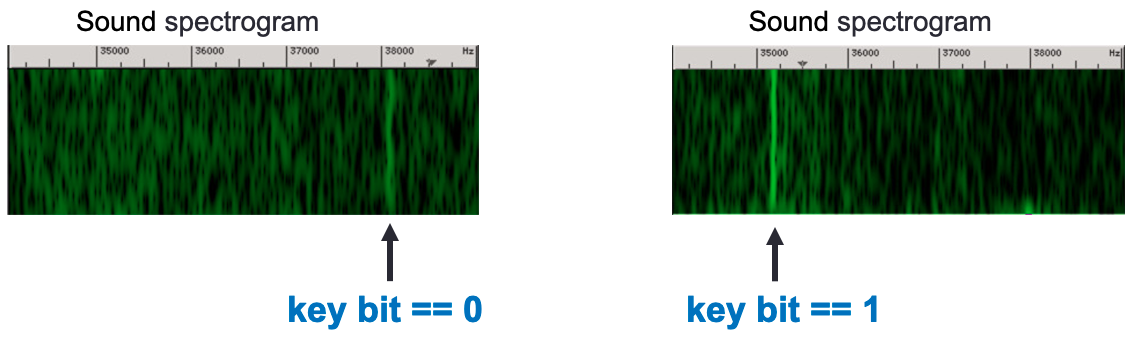
Timing side channel
1 | if (k == 1) then |
Break RSA with Timing Side Channel
square | square | square + multiply | square +
multiply | ...
0 | 0 | 1 | 1 | ...
fast | fast | slow | slow | ...
Break RSA with Power Side channel
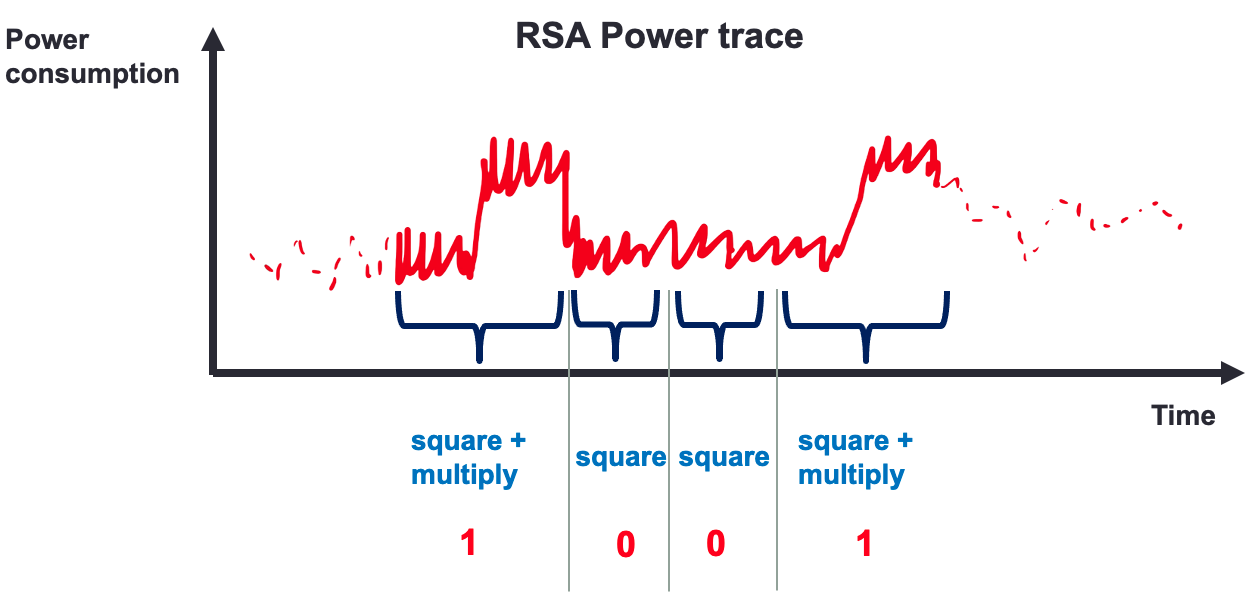
Break RSA with Power Side channel
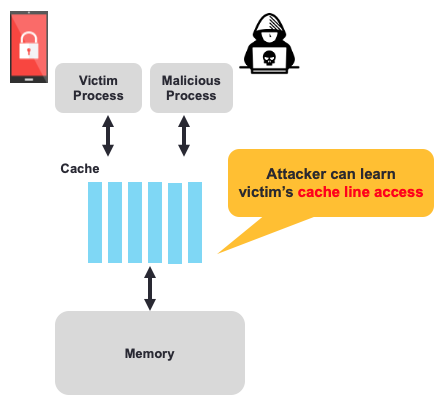
Cache-based side channel
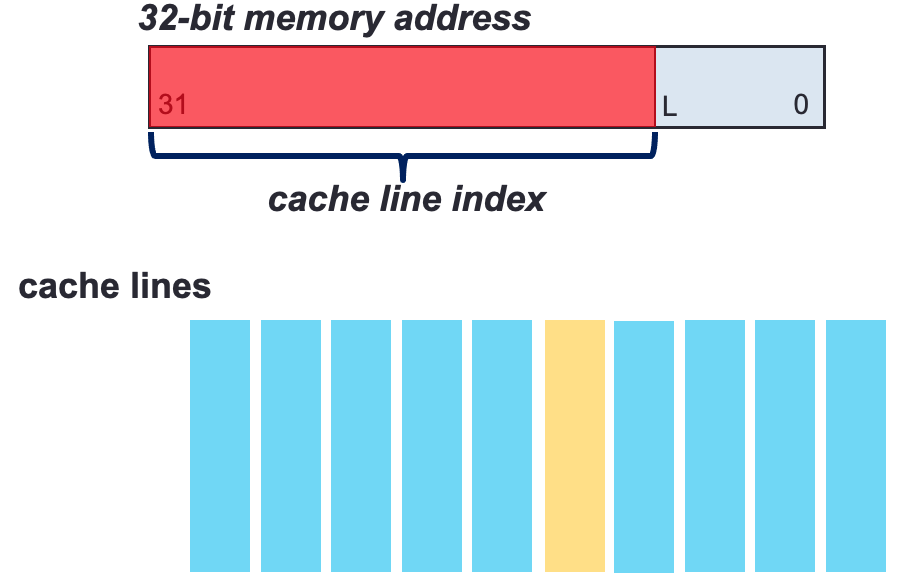
Cache lines: minimal storage units of a cache 64 bytes
Cache sets: equal number of cache lines
1 | // Table Lookup |
idx is virtual address, for L1 and L2 cache, virtual address is used for indexing, however for L3 cache, physical address is used.
The upper part of a memory address maps a memory access to a cache line access
Set index: locate the set in which the data may be stored.
Tag: confirm the data is present in one of its lines
The System model for a multi-core processor, L1 and L2 cache is private to each core and LLC is shared across multiple cores;
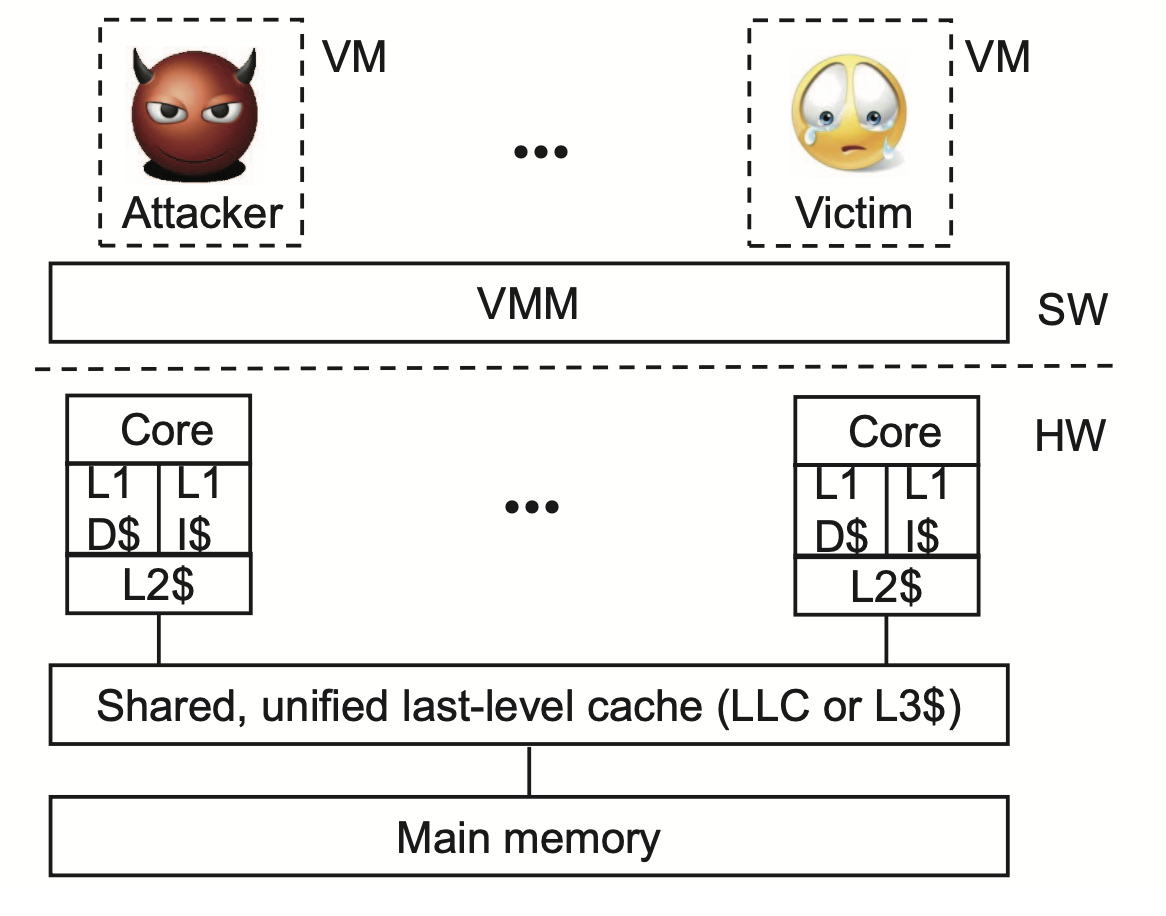
Threat model
Support
Meltdown
Spectre
L1 and L2 Cache Side Channel
Prime-and-Probe